Grant access to Azure Storage Accounts for Azure resource instances
@20aman Jan 05, 2022You can now grant access to resource instances to Azure Storage Accounts. This further secures and restricts storage account access only to your application's Azure resources.
Resource instances must be from the same tenant as your storage account, but they can belong to any subscription in the tenant. Internally it uses system-assigned managed identity for the selected Azure resources.
Granting access
Follow the below steps to set up access to Resource Instances:
- Step 1 - You can start by navigating to your Storage Account and then navigating to the Networking under "Security + networking"
- Step 2 - Scroll down to the section named "Resource instances"
- Step 3 - Select the Resource Type as per your requirements
- Step 4 - Select the instance name.
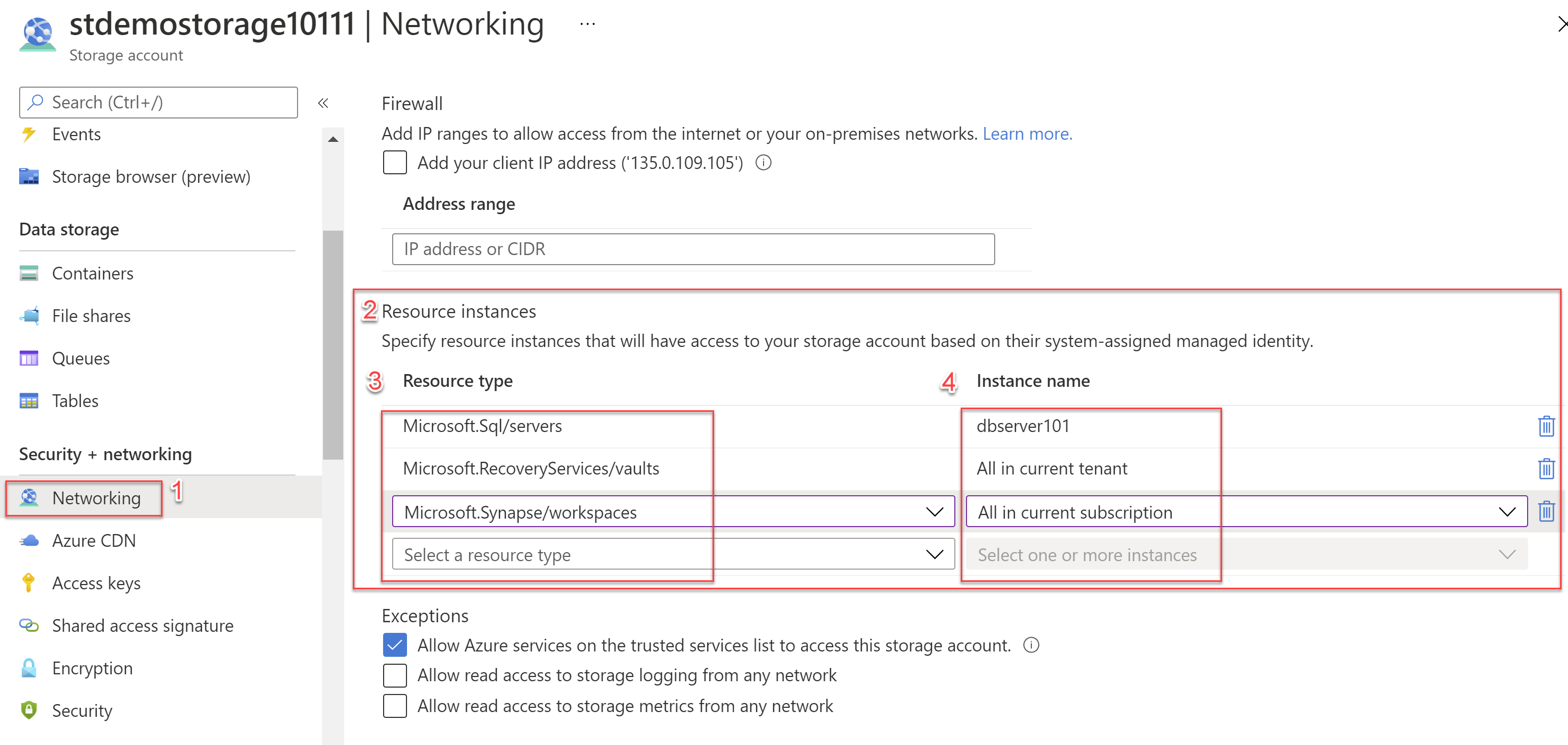
You have various options for the instance name selection:
- You can select an individual instance name.
- You can also select "All in current tenant" to select all resources of that type in the current tenant's all subscriptions.
- You can also select "All in current subscription" to select all resources of that type in the current subscription.
- You can also select "All in current resource group" to select all resources of that type in the current resource group.
Controlling allowed operations
The types of operations that a resource instance can perform on storage account data are determined by the Azure role assignments of the resource instance. You can assign these using the system-assigned managed identity of the resource on the Storage Account's RBAC settings.
Reference: You can read more on the official documentation here: Grant access from Azure resource instances