Simplifying Azure Bastion - 1 What is Azure Bastion
@20aman Apr 03, 2021This blog is a part of the Azure Bastion series. You can find the Index of this series here: Azure Bastion Series.
1. Details about Azure Bastion
Azure Bastion is a fully platform-managed PaaS service that provides RDP/SSH over TLS i.e. port 443 to all the VMs in the network. Think of this as a managed Jump Box or Jump Server service provided by Microsoft. The service is deployed via a managed host into your virtual network. This host is like a fully managed Jump box and is kept up to date by Microsoft.
Note that you will need to deploy one host for each of your virtual networks. Using one host, you will be able to connect to all the VMs in the same virtual network. The Bastion host needs a Public IP address. All the rest of the VMs don't need any public IP address.
Here are key points about Azure Bastion:
- Azure Bastion provides an integrated platform alternative to manually deploying and managing jump servers or Jump boxes to shield your virtual machines.
- It is a fully platform-managed PaaS service
- Bastion host is provisioned inside your virtual network
- Secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS
- Virtual machines do not need a public IP address, agent, or special client software
- One Bastion host is needed per virtual network
- The public IP of the Bastion resource on which RDP/SSH will be accessed (over port 443)
- You don't need an RDP or SSH client. Use the Azure portal to let you get RDP/SSH access to your virtual machine directly in the browser.
- Azure Bastion doesn't move or store customer data out of the region it is deployed in.
2. Shortcomings or Areas of Improvement
The below features are currently either not available or are not supported:
- IPv6 is not supported. Azure Bastion supports IPv4 only.
- Only text copy/paste is supported. Features, such as file copy, are not supported yet.
- It doesn't work with AADJ VM extension-joined machines using Azure AD users.
- Azure Bastion currently supports only en-us-qwerty keyboard layout inside the VM.
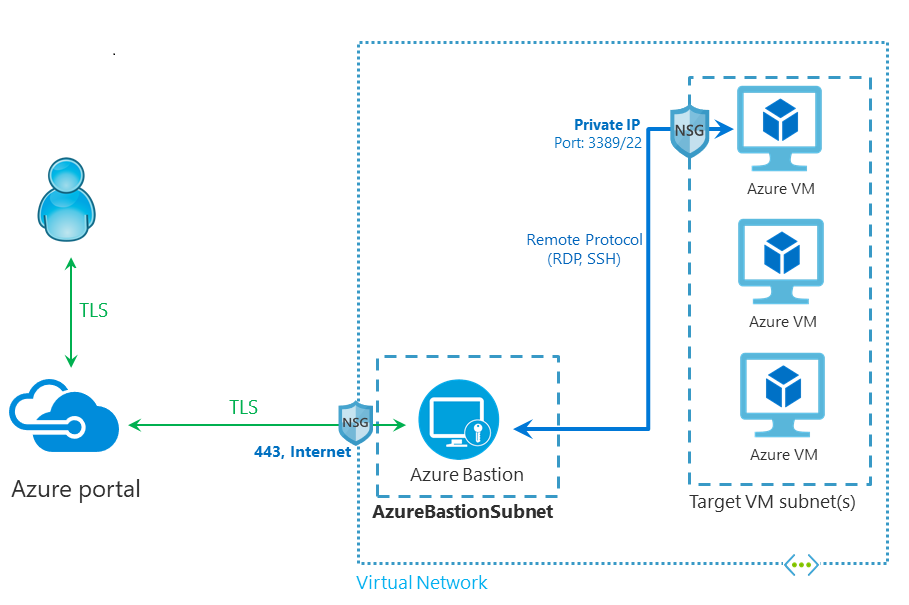
3. Architecture - How Azure Bastion works
Bastion Hosts are Jump servers that are deployed with a public IP address. These reside at the perimeter of your network. All the other VMs do not need any public IP address. You will be able to connect to the VMs via this Bastion host. The VMs can be deployed in one or many different subnets in the same virtual network.
You need to have a dedicated subnet with the name as AzureBastionSubnet. This subnet must be at least /27 or larger. This subnet should be deployed before creating the Bastion host.
You connect to the Bastion server directly from within the browser on port 443. The Bastion host in turn connects to the VM at port 3389 for RDP and 22 for SSH.
The subnet for the Azure Bastion host needs to have connectivity to the rest of the subnets. This is available by default. If you have NSGs then Bastion-related communication should be allowed. We will look at these rules in detail in a later post.
Note that UDR is not supported on an Azure Bastion subnet. You don’t need to force traffic from an Azure Bastion subnet to Azure Firewall because the communication between Azure Bastion and your VMs is private.
Microsoft keeps Azure Bastion hardened and always up to date for you to ensure that it can withstand attacks from outside.
4. Benefits of using Azure Bastion
There are various benefits of using Azure Bastion. The main one being able to RDP/SSH to your VMs without exposing them via any public IP address. Below is the list of various benefits of having Azure Bastion in your virtual networks:
- Secure and seamless RDP and SSH access to your virtual machines
- No Public IP exposure on the VM
- Help limit threats such as port scanning and other types of malware targeting your VMs
- Fully managed, autoscaling, and hardened PaaS service
- Uses a modern HTML5-based web client and standard SSL ports. This makes Firewall and other security rules very easy to manage.
- Existing authentication works i.e. Existing credentials and SSH keys will still be used for connecting to the VMs
- Same single pane of glass experience to connect to all the VMs
- Bastion host servers are designed and configured to withstand attacks. The Azure platform protects against zero-day exploits by keeping the Azure Bastion hardened and always up to date for you.
5. Concurrency Considerations
Both RDP and SSH are a usage-based protocol. High usage of sessions will cause the bastion host to support a lower total number of sessions. The numbers below assume normal day-to-day workflows.
| Workload Type* | Limit** |
|---|---|
| Light | 100 |
| Medium | 50 |
| Heavy | 5 |
These workload types are defined here: Remote Desktop workloads
6. Pricing
There are two components of the pricing related to Azure Bastion:
- Fixed charge for the service. This is the charge billed hourly for deploying the service. E.g. in an East US location, this charge is around $0.19 per hour.
- Outbound data transfer charges. This is the charge based on the total outbound data transfer. This is further tiered into various categories based on the total consumption.
The pricing details can be found here: Azure Bastion pricing
You can read more information about Azure Bastion in the official documentation here: Azure Bastion Overview.