Azure for AWS professionals - Networking - AWS - 04 Network ACLs
@20aman Oct 04, 2019Note that this post is a part of the series. You can view all posts in this series here: Azure for AWS professionals - Index
Network ACLs or Access Control Lists is like a firewall for your subnets. There are inbound and outbound rules defined in these ACLs that determine what traffic is allowed in a subnet and what traffic will be blocked. These are great for the security of your network.
To access the Network ACLs, navigate to the VPC section in AWS and then click on the "Network ACLs" option in the Security menu on the left.
You can view all your ACLs here. Select one and view its properties in the bottom panel. These properties include Details, Inbound rules, Outbound rules, Subnet associations and Tags. You can either right-click on the ACL or click on the Actions button to view the action that you can take on this ACL. The key actions we are interested in includes:
- Edit Subnet associations
- Edit Inbound rules
- Edit Outbound rules
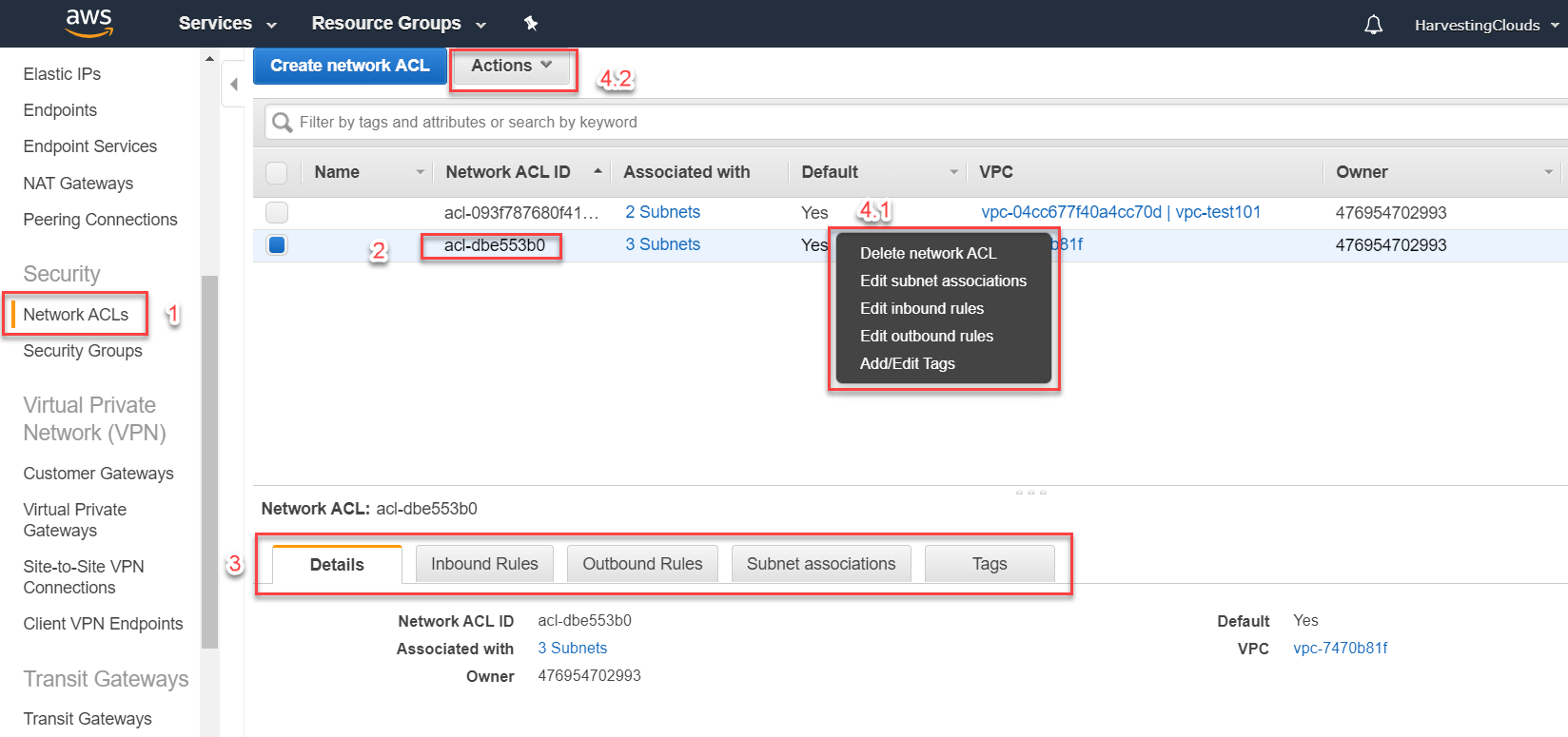
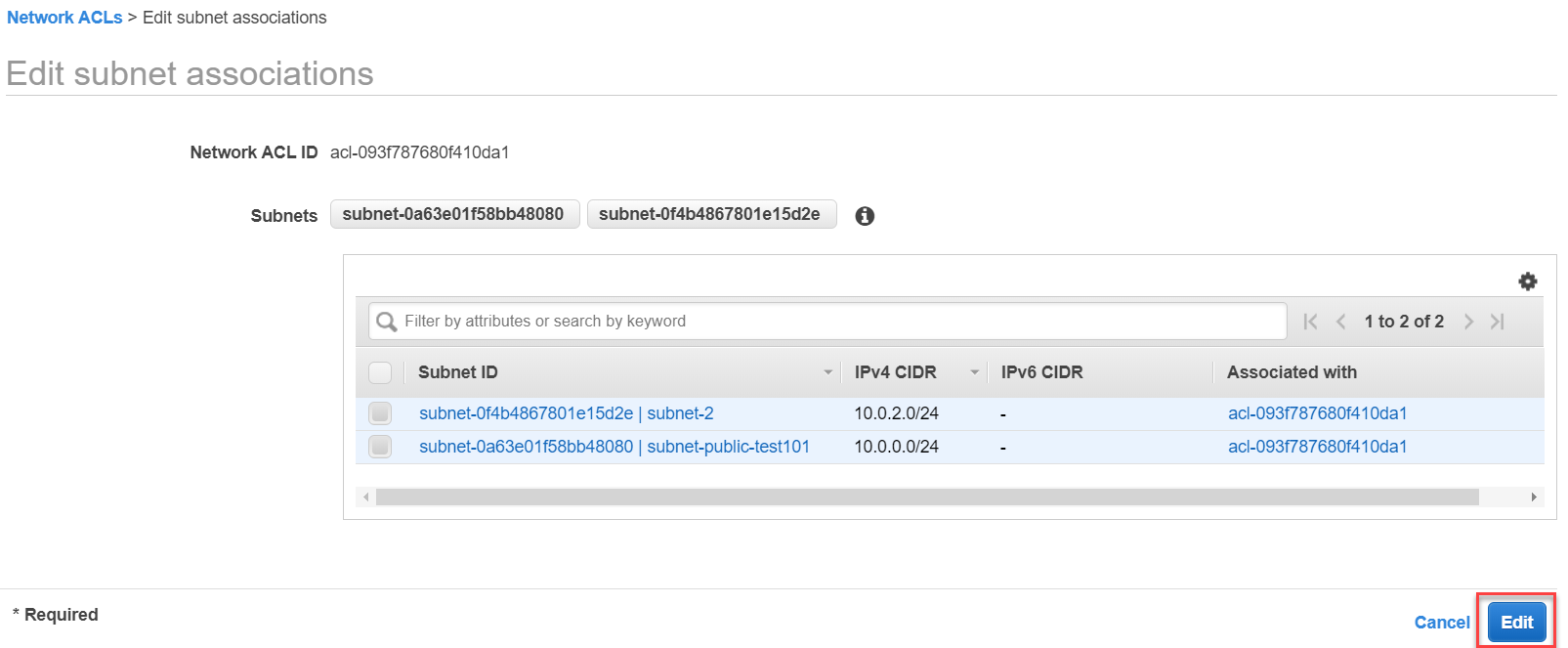
"Edit Subnet associations" option is to edit the linking of ACL to a subnet. You can associate an ACL to one or multiple subnets.
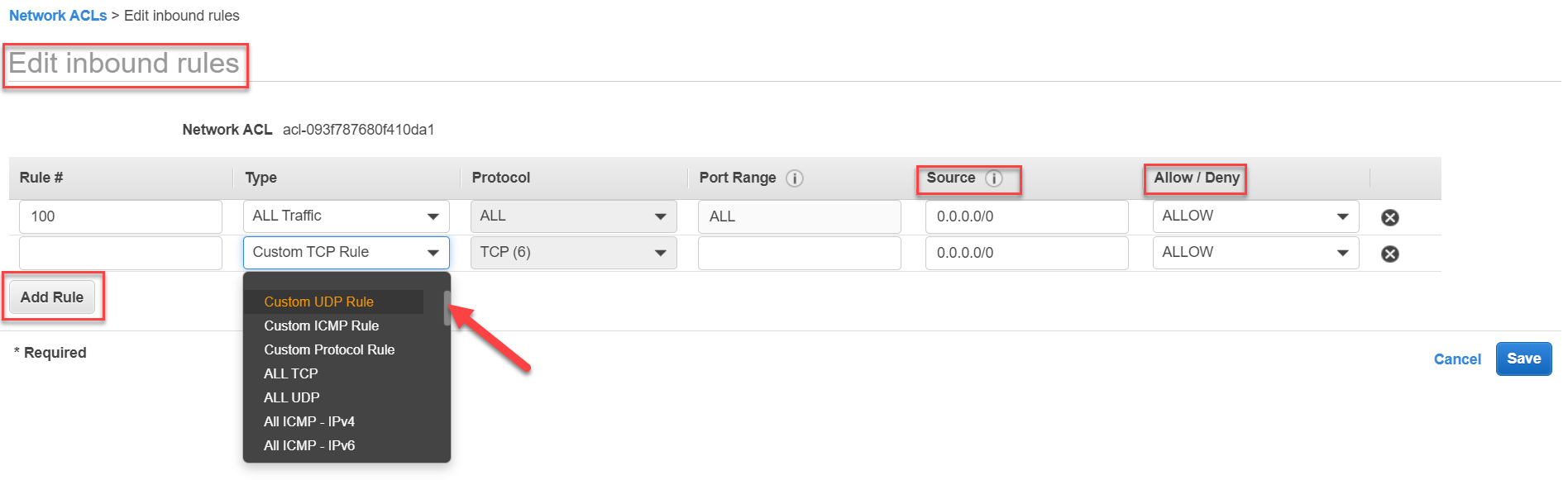
"Edit Inbound rules" option is to edit the inbound rules. These govern what traffic will be allowed coming into the subnet. Each rule contains:
- Rule number or Rule # - this is the order in which the rules are executed.
- Type - this determines the protocol or type of traffic. You have loads of pre-defined types, or you can add a custom option from the list
- Protocol - this is determined by the type
- Port Range - this is also dependent on the type selected. For pre-defined types, this is auto-populated. For custom type, you can define a custom port range.
- Source - this is the place from where the communication will originate (that is coming into the associated subnet)
- Allow/Deny - this determines if the inbound communication defined by your rule will be allowed or denied.
"Edit Outbound rules" option is to edit the outbound rules. These govern what traffic will be allowed coming out of the subnet. These rules are very similar to the inbound rules. The only difference is that now the traffic is originating from within this subnet and is going outbound. Hence we need to specify a Destination (instead of a Source) while defining the outbound rules.
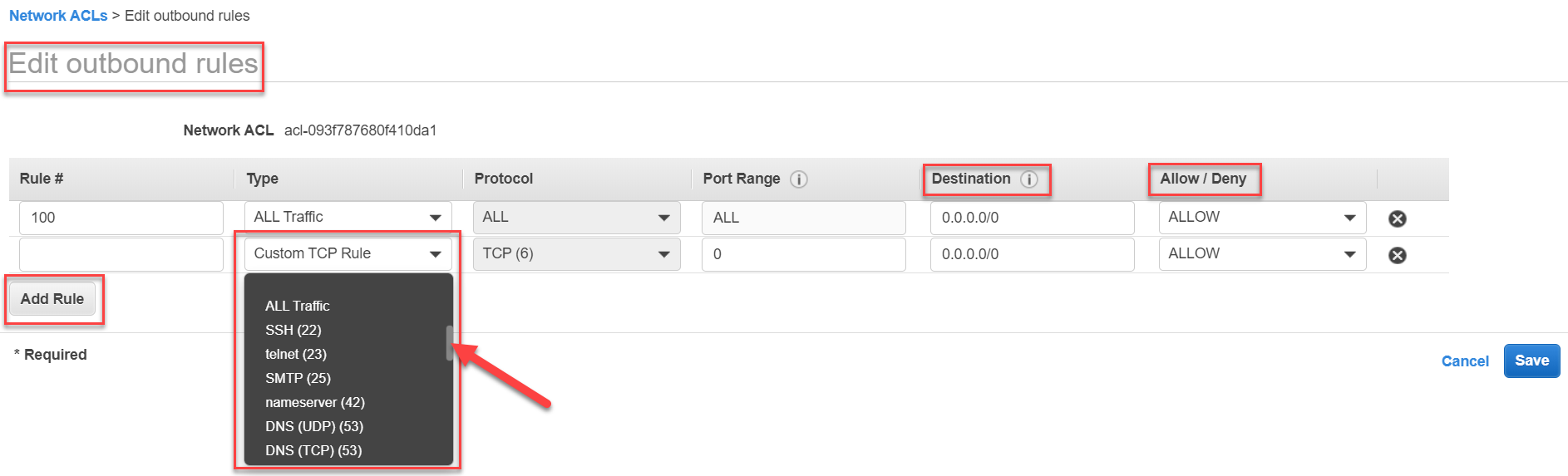
Please Note that the address "0.0.0.0/0" means all IP addresses. This can be used for Source in inbound rules or Destination for outbound rules, if the exact IP address or IP address range is unknown. Although this should be used with caution. As a best practice, this should be avoided at all costs and should be replaced with as small IP address ranges as possible.