Block all public access to Azure Storage Accounts - via manual setting
@20aman Jul 15, 2021In the recent past, there have been so many instances where critical data was unintentionally exposed because public access was enabled on the Azure Storage Accounts. Outside people were able to access the blobs and containers publically. Now there is a way to block all public access with just a click of a button.
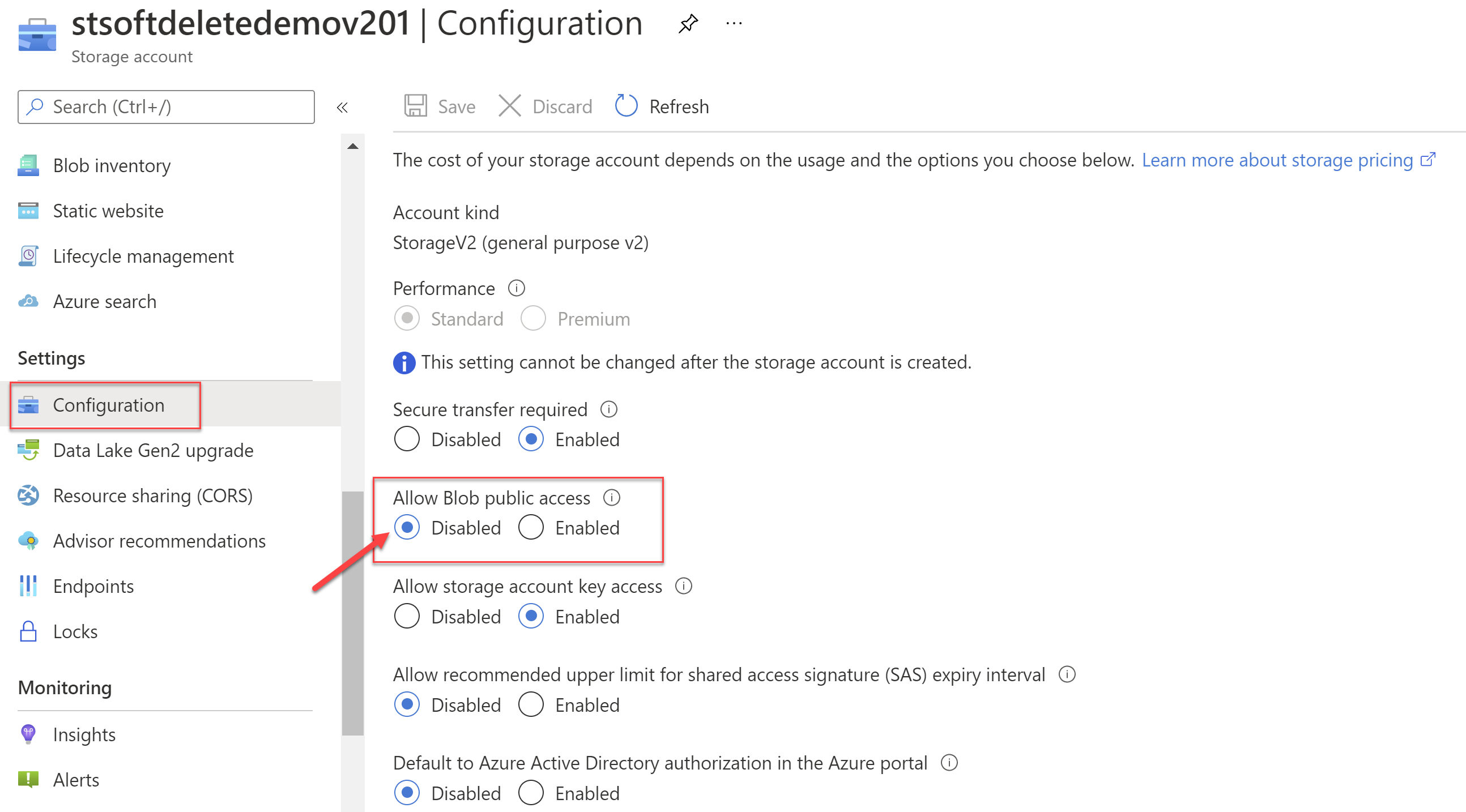
Finding the setting - Allow blob public access
To find this setting, navigate to the storage account for which you want to enable this setting. Then navigate to Configuration under Settings. Find the configuration for "Allow Blob public access" and set it to "Disabled" to disable any public blob access.
More ways to secure the storage account
There are various ways to further lockdown and secure your storage account. Let's look at a few of these.
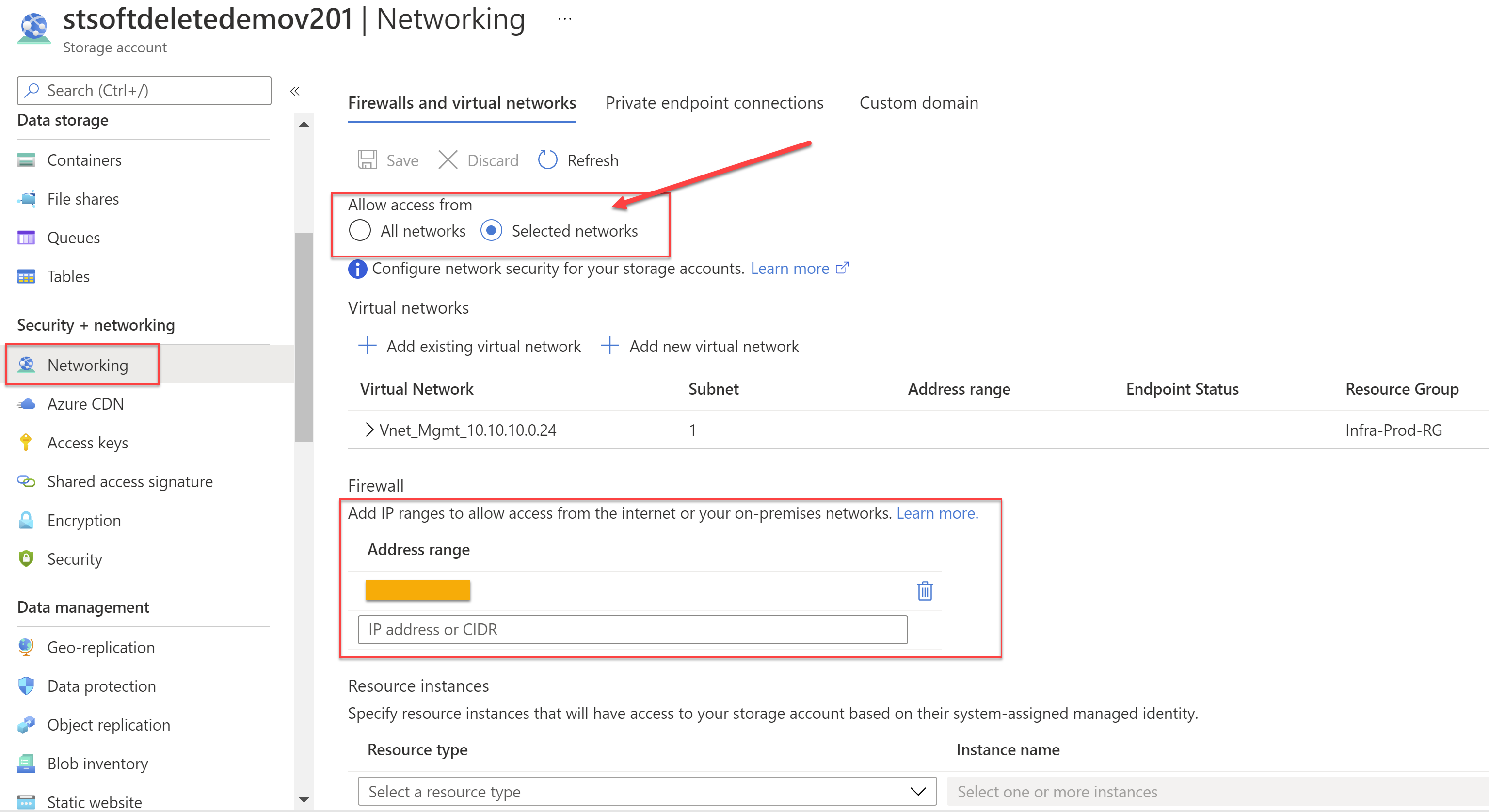
Locking the Networking to only selected networks
One of the most important settings is to update the Storage Account's networking settings to not allow access from "All Networks". You should lock it down to specific networks only or to specified Public IP addresses only.
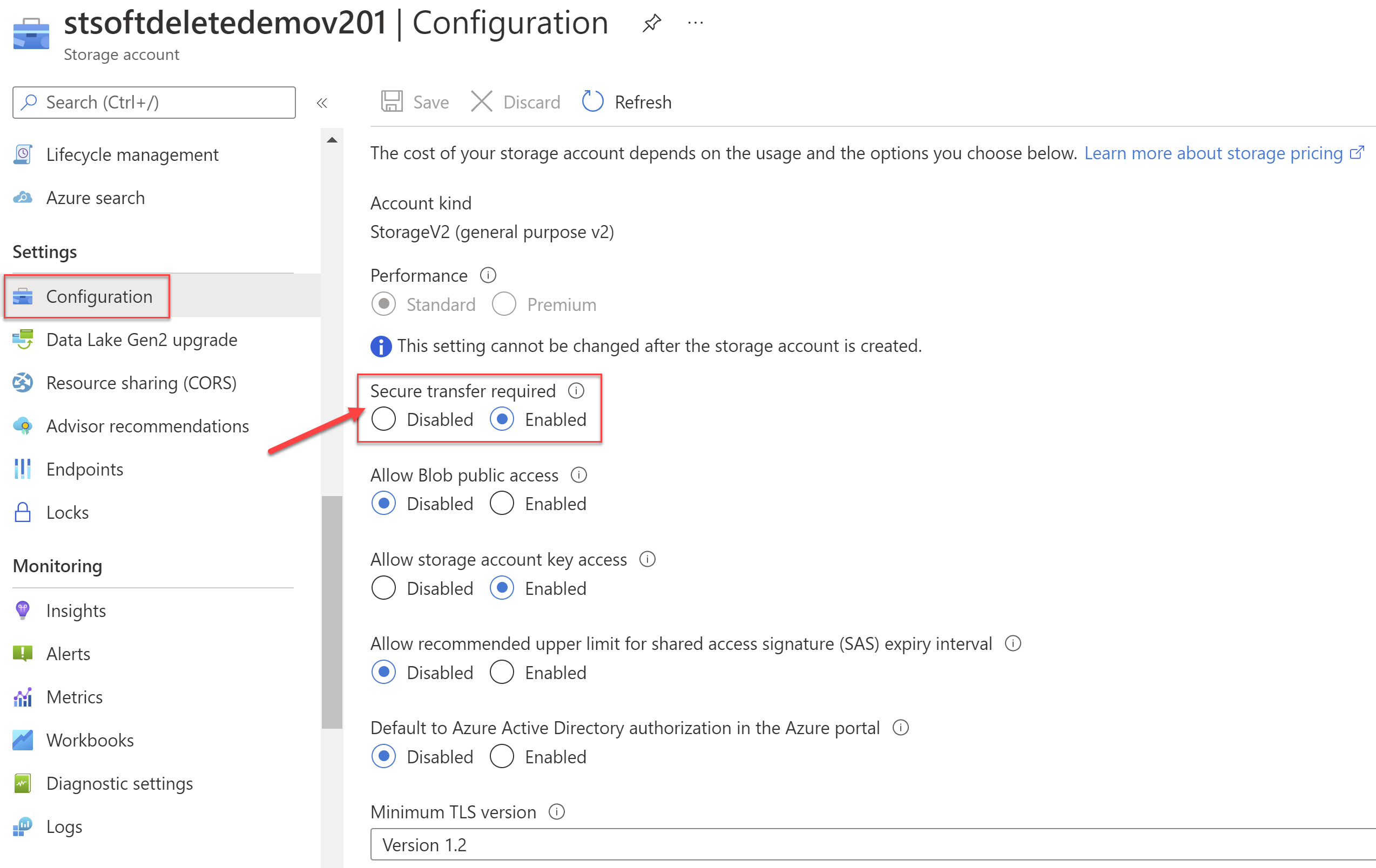
Other security related settings
Another security-related configuration is to require secure transfer. This means that when the data travels to and from the storage account HTTPS should be used instead of HTTP. In the case of file shares, the encrypted connection should be used as well.
Next Steps
In the next post, we will look at automatically enforcing blocking of the public access to storage accounts across your subscription with Azure policies. We will have this policy apply for any existing and new Storage Accounts. You can view that post here: Block all public access to Azure Storage Accounts - via Azure policy - with complete sample.
Reference: Prevent anonymous public read access to containers and blobs