Demystifying Azure Security - Azure SQL Database - Dynamic Data Masking
@20aman Mar 11, 2018This blog post is part of the Demystifying Azure Security series. All posts in the series can be found here: Demystifying Azure Security - Series Index
Dynamic Data Masking is a feature of Azure SQL Databases, that allows you to hide the sensitive data. E.g. your database contains information regarding the Credit Cards of your customers. When exposing the database you want to ensure that the credit cards are not exposed. They should automatically be presented in the format "xxxx-xxxx-xxxx-1234" i.e. only exposing the last 4 digits.
Feature Basics
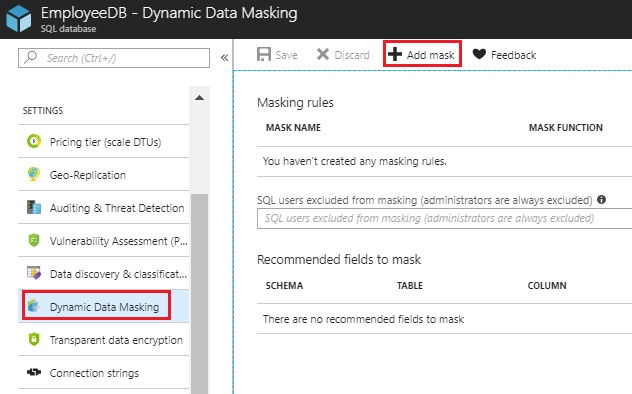
This feature can be accessed by navigating to your database and then clicking on the "Dynamic Data Masking" option under settings. By default, there are no masks applied. Click on "+ Add mask" to add a new mask.
Note that whatever masks you apply are not applied to the administrators. Additionally, you can provide the SQL users who should be excluded from masking.
Azure SQL Database will also automatically try to recommend the fields that should be masked.
Adding Masking Rules
When adding Masking Rules you provide below information:
- Name for the mask is auto-populated (based on your selections)
- Schema
- Table in that schema
- Column in the table, where mask should be applied
- Masking Criteria
Note that the Masking criteria vary based on the type of the column. E.g. If a column does not have numerical value then the masking criteria for "Number (random number range)" will show as disabled.
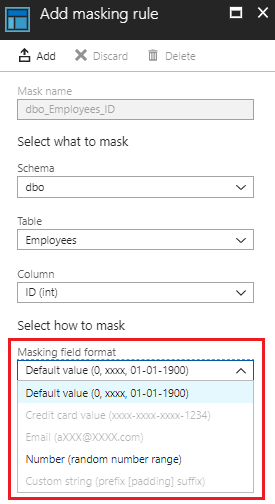
The different masking criteria that you can apply are:
- Default value (0, xxxx, 01-01-1900)
- Credit Card value (xxxx-xxxx-xxxx-1234)
- Email (aXXX@XXXX.com)
- Number (random number range)
- Custom string (prefix [padding] suffix)