Demystifying Azure Security - Azure SQL Database - Firewall Rule for Virtual Networks
@20aman Mar 04, 2018This blog post is part of the Demystifying Azure Security series. All posts in the series can be found here: Demystifying Azure Security - Series Index
Before going through this blog, please make sure you have covered these:
- Set Server Firewall for Azure SQL Databases
- Service Endpoints for Azure SQL on Virtual Network. Note that this is pre-requisite for the firewall rules to be configured on the Virtual Network level.
Setting up the Firewall Rule for Virtual Networks, at the SQL Server level, enables you to allow access to a subnet in a Virtual Network in Azure on all the SQL Databases on the SQL Server. The firewall rules are always set at the server level, hence any rule you put will allow access on all the databases on the SQL Server.
Setting up the Rules is very simple. You navigate to the firewall settings for the SQL Database/SQL Server (as discussed in the previous blog). Then you focus on the lower section on the blade for Virtual Network Firewall rules as shown below.
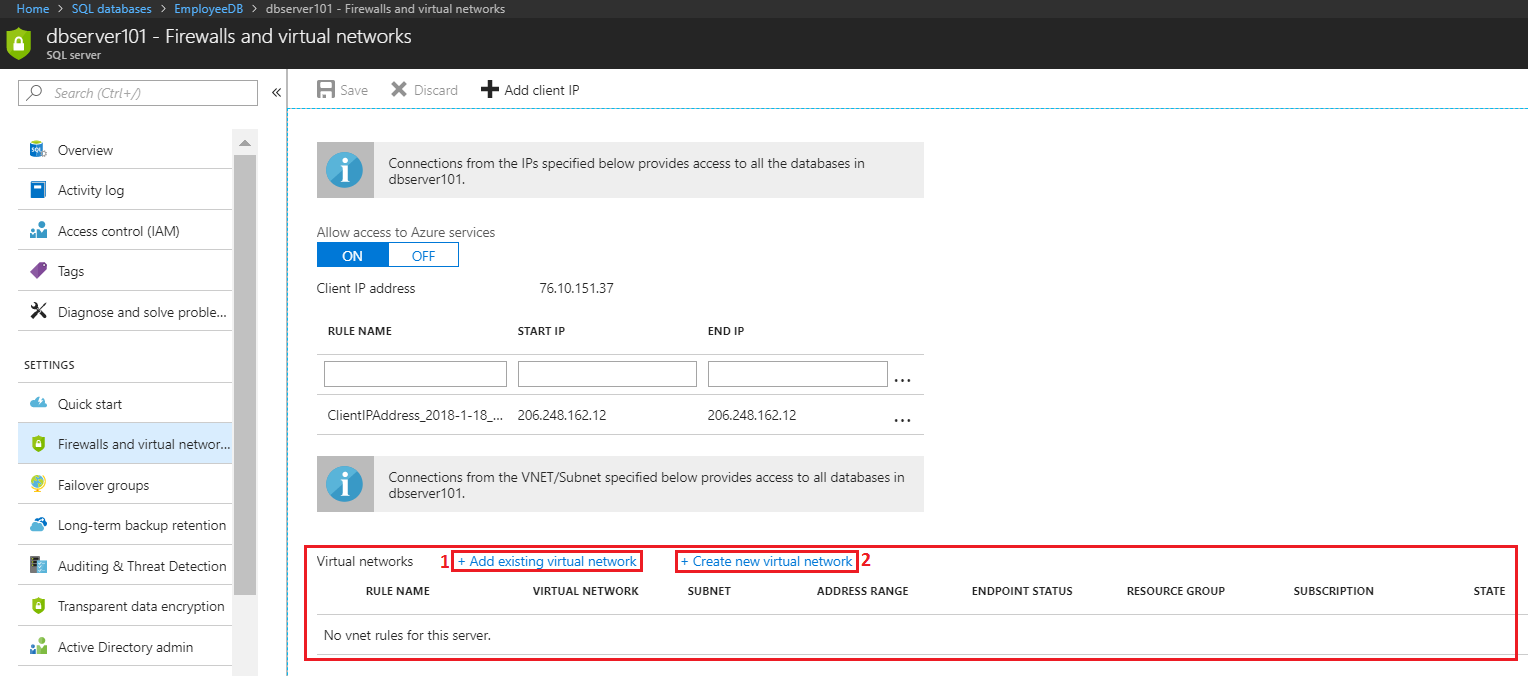
Note that you can:
- Add existing virtual network
- Create a new virtual network (and provide access)
As a best practice, you should plan the virtual network and subnets before the configurations on the SQL Server Firewall.
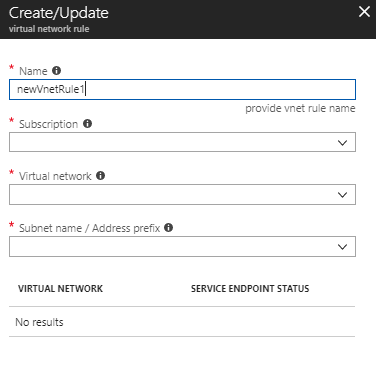
When you click on "Add existing virtual network" you are presented with the below wizard. Here you select:
- The name for the rule. This could be any descriptive name for the rule.
- The Subscription where the virtual network exists
- Virtual network where you want to allow the access
- Subnet name within the Virtual network where you want to allow the access
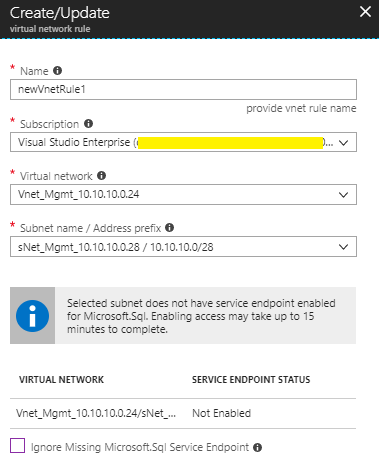
Below, is the screenshot of the rule with values populated. If the Service Endpoint is not enabled for the "Microsoft.Sql" provider then you will view a message for the same and the wizard will attempt to enable the same.
Thats all there is to it. Just hit Ok and then hit Save to apply the rule.