Windows Admin Center in the Azure portal - 9 Securing inbound connectivity
@20aman Mar 06, 2022This blog is a part of the Windows Admin Center in the Azure portal series. You can find the Index of this series here: Windows Admin Center in the Azure portal.
The security concern
As we saw in one of the previous posts, when setting up Windows Admin Center it opens the inbound connectivity on the port specified for "Any" Source. This is shown in the Inbound security rules of the Network Security Group (NSG) for the VM.
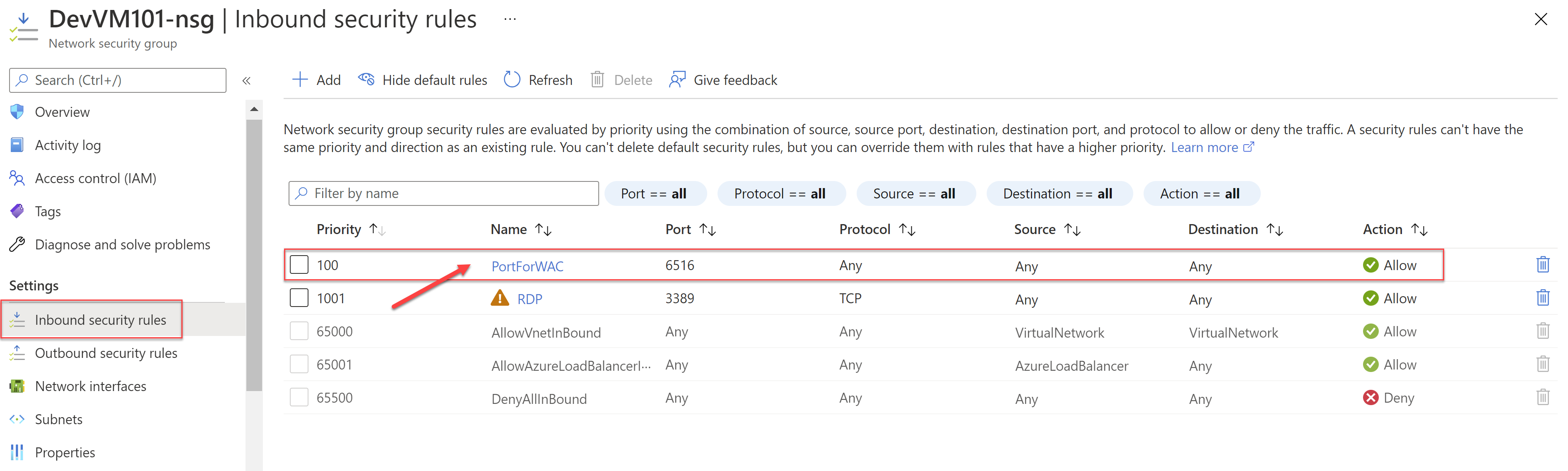
This is a potential security risk as it leaves the system vulnerable and the port open for access for all attackers on the public internet.
The Solution #1
The solution is very simple. The solution is to lock it down to only a specific IP address or a range of IP addresses. This limits which IP addresses can access Windows Admin Center on the VM.
To be able to do this, you will need to update the Inbound rule on the Network Security Group as shown above and then update the "Source" for the rule. Instead of "Any" change that to the public IP address of the VM from where you are connecting to the Windows Admin Center (within Azure portal). If you know a range of IPs that you will be using then you can specify the range instead.
How to find your current Public IP address
Your ISP will provide you with a dynamic public IP address (unless you purchased a static public IP). To be able to find your public IP address just search for "what is my IP address" and you will find many third-party websites that will show you your current public IP address and possible geographic location. One such website is provided below, just as a reference:
The Solution #2
The second solution is to simply remove the inbound NSG rule and allow access only on the private IP address. This would mean that you would need to have connectivity to the VM's virtual network from where you are trying to access the Windows Admin Center on the VM (via Azure portal).
This is a much more secure solution and ensures that there is no connectivity allowed from the public IP to the VM.